Check Point Infinity Architecture The only fully consolidated cyber security architecture that provides unprecedented protection against Gen V mega-cyberattacks as well as future cyber threats across all networks, endpoint, cloud and mobile. Check Point provides organizations of all sizes with the latest data and network security protection in an integrated next generation firewall platform, reducing complexity and lowering the total cost of ownership. Hyperscale Network Security is the most cost effective approach to minimizing risk and scaling on demand.
In This Section: |
Overview of Firewall Features
Firewalls control the traffic between the internal and external networks and are the core of a strong network security policy. Check Point Software Blades are a set of security features that makes sure that the Security Gateway or Security Management Server gives the correct functionality and performance. The Check Point Firewall is part of the Software Blade architecture that supplies 'next-generation' firewall features, including:
- VPN and mobile device connectivity
- Identity and computer awareness
- Internet access and filtering
- Application control
- Intrusion and threat prevention
- Data Loss Prevention
Components of the Check Point Solution
Item | Description |
|---|---|
1 | Internet and external networks |
Security Gateway | |
3 | SmartDashboard |
4 | Security Management Server |
5 | Internal network |
These are the primary components of a Check Point solution:
- Security Gateway - The engine that enforces the organization's security policy, is an entry point to the LAN, and is managed by the Security Management Server.
- Security Management Server - The application that manages, stores, and distributes the security policy to Security Gateways.
- SmartDashboard - A Check Point client used to create and manage the security policy.
Dual Stack (IPv4 and IPv6) Network Configuration
You can easily configure the Firewall to support a dual stack network that uses IPv4 and IPv6 addresses. Configure one or more interfaces with the applicable IPv4 and IPv6 addresses.
Item | Description |
|---|---|
IPv4 network traffic | |
IPv6 network traffic | |
1 | Security Gateway for dual stack network |
2 | Internal network (IPv6 traffic) |
3 | Dual stack web server in the DMZ |
4 | Security Gateway for IPv4 network |
5 | Security Gateway for IPv6 network |
6 | Mobile device (IPv4 traffic) |
7 | Mobile devices (IPv6 traffic) |
Note - For R76 Security Gateways and higher, you can configure the interfaces to use only IPv6 addresses. |
Access Control and the Rule Base
A primary goal of a firewall is to control access and traffic to and from the internal and external networks. The Firewall lets system administrators securely control access to computers, clients, servers and applications. The Firewall Rule Base defines the quality of the access control and network performance. Rules that are designed correctly make sure that a network:
- Only allows authorized connections and prevents vulnerabilities in a network
- Gives authorized users access to the correct internal networks
- Optimizes network performance and efficiently inspects connections
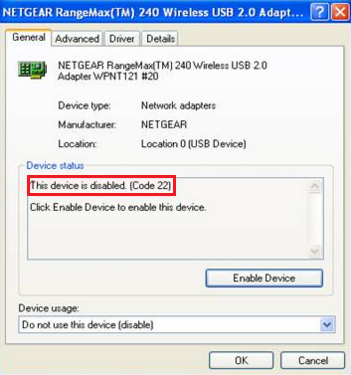
Licenses
Some LTE features require special licenses installed on the Security Gateways. The management server does not require special licenses.
- GTP features require a Carrier license, or the earlier GX/GTP license.
- CGNAT requires the Carrier license.
- SCTP and Diameter inspection require the Carrier license.
If there is no Carrier license on the Security Gateway, you cannot install a policy that has these rules:
- CGNAT rules
- Rules with SCTP or Diameter services
- Rules with Service = Any and Match for any attribute is enabled for an SCTP service.
Notes
- Services defined in Services > Other do not require a Carrier license.
- SCTP Connections matching Other services are not inspected.
How to Use this Guide
When you configure a Firewall, it is necessary that you understand how it is connected to the other Software Blades. For example, you must add a rule for the Firewall to allow remote users to connect to the internal network. In addition, you can enable Software Blades to supply advanced protection for the network, such as IPS and Anti-Bot.
Some of the sections in this guide tell you how to enable a sample configuration of a Software Blade. Make sure that you read the applicable Administration Guide for the Software Blade before you configure the feature for a production environment. Each section also explains rules that you must add to the Firewall Rule Base to complete the configuration for that feature.
Software Blades in this Guide
Software | Blade | Chapter |
|---|---|---|
Firewall | ||
Mobile Access | ||
IPsec VPN | ||
Identity Awareness | ||
URL Filtering | ||
Application Control | ||
IPS | ||
Anti-Bot | ||
Anti-Virus | ||
Anti-Spam | ||
Data Loss Prevention | ||
Advanced Networking & Clustering | ||
SmartEvent | ||
SmartLog |
SmartDashboard Toolbar
You can use the SmartDashboard toolbar to do these actions:
Icon | Description |
|---|---|
Open the SmartDashboard menu. When instructed to select menu options, click this button to show the menu. For example, if you are instructed to select Manage > Users and Administrators, click this button to open the Manage menu and then select the Users and Administrators option. | |
Save current policy and all system objects. | |
Open a policy package, which is a collection of Policies saved together with the same name. | |
Refresh policy from the Security Management Server. | |
Open the Database Revision Control window. | |
Change global properties. | |
Verify Rule Base consistency. | |
Install the policy on Security Gateways or VSX Gateways. | |
Open SmartConsole. |
Schedule:
This is the current state of Mobile Access support in Windows 10 and the plans to complete it:
Note: The schedule provided below is subject to modifications. For most up-to-date information, revisit this page, or sign up for RSS feed regarding this solution (at the top).
| Internet Explorer 11 | Microsoft Edge | Firefox | Chrome | |
| Mobile Access Portal | Supported | Supported | Supported | Supported |
| SSL Network Extender (SNX) Network Mode | Refer to Hotfix #1 | Not Supported (1) | Supported | Partially Supported (2) |
| SSL Network Extender (SNX) Application Mode | Supported | Not Supported (1) | Supported | Partially Supported (2) |
| Endpoint Security On Demand (ESOD) Compliance Scanner | Refer to Hotfix #1 | Not Supported (1) | Refer to Hotfix #1 | Partially Supported (3) |
| Endpoint Security On Demand Secure Workspace (SWS) | Refer to Hotfix #1 | Not Supported (1) | Refer to Hotfix #1 | Partially Supported (3) |
Notes:
- Please refer to sk113410 - Mobile Access Portal and Java Compatibility that outlines Check Point's new Mobile Access Portal Agent technology.
- SSL Network Extender support for Chrome:
- For Chrome builds lower than 45:
Follow sk106021 - 'Java is unavailable' error in Google Chrome when trying to use SSL Network Extender (SNX), Secure Workspace and the Endpoint Compliance scanner. - For Chrome builds 45 and above:
Please refer to sk113410 - Mobile Access Portal and Java Compatibility.
- For Chrome builds lower than 45:
- Endpoint Security On Demand support for Chrome:
- For Chrome builds lower than 45:
Hotfix #1 is required in addition tosk106021 - 'Java is unavailable' error in Google Chrome when trying to use SSL Network Extender (SNX), Secure Workspace and the Endpoint Compliance scanner. - For Chrome builds 45 and above:
Hotfix #1 will not provide the required support. Please refer to sk113410 - Mobile Access Portal and Java Compatibility.
- For Chrome builds lower than 45:
Hotfix availability:
| Target | Hotfix |
| R80.30 | For a Hotfix for R80.20, please refer to sk113410. |
| R80.20 | For a Hotfix for R80.20, please refer to sk113410. |
| R80.10 | For a Hotfix for R80.10, please refer to sk113410. |
| R77.30 | Hotfix for R77.30 GA only can be downloaded directly from this article - refer to 'Hotfix #1' below. |
| |
| R77.20 |
|
| R77.10 and lower | For any supported version, contact Check Point Support to get this Hotfix. A Support Engineer will make sure the Hotfix is compatible with your environment before providing the Hotfix. For faster resolution and verification, please collect CPinfo files from the Security Management Server and Mobile Access Gateways involved in the case. |
| SMB appliances 600 / 700 / 1100 / 1200R / 1400 | Fixed in R77.20.40 for all locally managed devices, starting from R77.20.11. Note:
|
| R77.30 and lower with any existing hotfixes | If any hotfixes are currently installed on the target machine, then for any supported version contact Check Point Support to get this Hotfix. A Support Engineer will make sure the Hotfix is compatible with your environment before providing the Hotfix. For faster resolution and verification, please collect CPinfo files from the Security Management Server and Mobile Access Gateways involved in the case. |
Note: Hotfix is integrated in R80.40 and above.
Check Point Network & Wireless Cards Drivers
Hotfix installation instructions:
In order to download these hotfix packages you will need to have a Software Subscription or Active Support plan.
- Show / Hide installation instructions for Hotfix #1 - support for Internet Explorer 11, Firefox and Chrome (builds lower than 45)
Hotfix has to be installed on Mobile Access Gateway.
Note: In cluster environment, this procedure must be performed on all members of the cluster.Download this hotfix package to your computer.
- Transfer the hotfix package to the Mobile Access Gateway (into some directory, e.g., /some_path_to_fix/).
Unpack and install the hotfix package:
[Expert@HostName]# cd /some_path_to_fix/
Note: The script will stop all of Check Point services (cpstop) - read the output on the screen.
[Expert@HostName]# tar -zxvf Check_Point_R77.30_Linux_sk107132.tgz
[Expert@HostName]# ./UnixInstallScriptReboot the Mobile Access Gateway.
UnInstall Instructions:
Note: In cluster environment, this procedure must be performed on all members of the cluster.
- Download and unpack the hotfix package (refer to the 'Installation instructions' above) above).
- Run the installation script with '-u' flag:
[Expert@HostName]# ./UnixInstallScript -u - Reboot the Mobile Access Gateway.
Related solutions:
Revision History:
Check Point Network & Wireless Cards Drivers

Licenses
Some LTE features require special licenses installed on the Security Gateways. The management server does not require special licenses.
- GTP features require a Carrier license, or the earlier GX/GTP license.
- CGNAT requires the Carrier license.
- SCTP and Diameter inspection require the Carrier license.
If there is no Carrier license on the Security Gateway, you cannot install a policy that has these rules:
- CGNAT rules
- Rules with SCTP or Diameter services
- Rules with Service = Any and Match for any attribute is enabled for an SCTP service.
Notes
- Services defined in Services > Other do not require a Carrier license.
- SCTP Connections matching Other services are not inspected.
How to Use this Guide
When you configure a Firewall, it is necessary that you understand how it is connected to the other Software Blades. For example, you must add a rule for the Firewall to allow remote users to connect to the internal network. In addition, you can enable Software Blades to supply advanced protection for the network, such as IPS and Anti-Bot.
Some of the sections in this guide tell you how to enable a sample configuration of a Software Blade. Make sure that you read the applicable Administration Guide for the Software Blade before you configure the feature for a production environment. Each section also explains rules that you must add to the Firewall Rule Base to complete the configuration for that feature.
Software Blades in this Guide
Software | Blade | Chapter |
|---|---|---|
Firewall | ||
Mobile Access | ||
IPsec VPN | ||
Identity Awareness | ||
URL Filtering | ||
Application Control | ||
IPS | ||
Anti-Bot | ||
Anti-Virus | ||
Anti-Spam | ||
Data Loss Prevention | ||
Advanced Networking & Clustering | ||
SmartEvent | ||
SmartLog |
SmartDashboard Toolbar
You can use the SmartDashboard toolbar to do these actions:
Icon | Description |
|---|---|
Open the SmartDashboard menu. When instructed to select menu options, click this button to show the menu. For example, if you are instructed to select Manage > Users and Administrators, click this button to open the Manage menu and then select the Users and Administrators option. | |
Save current policy and all system objects. | |
Open a policy package, which is a collection of Policies saved together with the same name. | |
Refresh policy from the Security Management Server. | |
Open the Database Revision Control window. | |
Change global properties. | |
Verify Rule Base consistency. | |
Install the policy on Security Gateways or VSX Gateways. | |
Open SmartConsole. |
Schedule:
This is the current state of Mobile Access support in Windows 10 and the plans to complete it:
Note: The schedule provided below is subject to modifications. For most up-to-date information, revisit this page, or sign up for RSS feed regarding this solution (at the top).
| Internet Explorer 11 | Microsoft Edge | Firefox | Chrome | |
| Mobile Access Portal | Supported | Supported | Supported | Supported |
| SSL Network Extender (SNX) Network Mode | Refer to Hotfix #1 | Not Supported (1) | Supported | Partially Supported (2) |
| SSL Network Extender (SNX) Application Mode | Supported | Not Supported (1) | Supported | Partially Supported (2) |
| Endpoint Security On Demand (ESOD) Compliance Scanner | Refer to Hotfix #1 | Not Supported (1) | Refer to Hotfix #1 | Partially Supported (3) |
| Endpoint Security On Demand Secure Workspace (SWS) | Refer to Hotfix #1 | Not Supported (1) | Refer to Hotfix #1 | Partially Supported (3) |
Notes:
- Please refer to sk113410 - Mobile Access Portal and Java Compatibility that outlines Check Point's new Mobile Access Portal Agent technology.
- SSL Network Extender support for Chrome:
- For Chrome builds lower than 45:
Follow sk106021 - 'Java is unavailable' error in Google Chrome when trying to use SSL Network Extender (SNX), Secure Workspace and the Endpoint Compliance scanner. - For Chrome builds 45 and above:
Please refer to sk113410 - Mobile Access Portal and Java Compatibility.
- For Chrome builds lower than 45:
- Endpoint Security On Demand support for Chrome:
- For Chrome builds lower than 45:
Hotfix #1 is required in addition tosk106021 - 'Java is unavailable' error in Google Chrome when trying to use SSL Network Extender (SNX), Secure Workspace and the Endpoint Compliance scanner. - For Chrome builds 45 and above:
Hotfix #1 will not provide the required support. Please refer to sk113410 - Mobile Access Portal and Java Compatibility.
- For Chrome builds lower than 45:
Hotfix availability:
| Target | Hotfix |
| R80.30 | For a Hotfix for R80.20, please refer to sk113410. |
| R80.20 | For a Hotfix for R80.20, please refer to sk113410. |
| R80.10 | For a Hotfix for R80.10, please refer to sk113410. |
| R77.30 | Hotfix for R77.30 GA only can be downloaded directly from this article - refer to 'Hotfix #1' below. |
| |
| R77.20 |
|
| R77.10 and lower | For any supported version, contact Check Point Support to get this Hotfix. A Support Engineer will make sure the Hotfix is compatible with your environment before providing the Hotfix. For faster resolution and verification, please collect CPinfo files from the Security Management Server and Mobile Access Gateways involved in the case. |
| SMB appliances 600 / 700 / 1100 / 1200R / 1400 | Fixed in R77.20.40 for all locally managed devices, starting from R77.20.11. Note:
|
| R77.30 and lower with any existing hotfixes | If any hotfixes are currently installed on the target machine, then for any supported version contact Check Point Support to get this Hotfix. A Support Engineer will make sure the Hotfix is compatible with your environment before providing the Hotfix. For faster resolution and verification, please collect CPinfo files from the Security Management Server and Mobile Access Gateways involved in the case. |
Note: Hotfix is integrated in R80.40 and above.
Check Point Network & Wireless Cards Drivers
Hotfix installation instructions:
In order to download these hotfix packages you will need to have a Software Subscription or Active Support plan.
- Show / Hide installation instructions for Hotfix #1 - support for Internet Explorer 11, Firefox and Chrome (builds lower than 45)
Hotfix has to be installed on Mobile Access Gateway.
Note: In cluster environment, this procedure must be performed on all members of the cluster.Download this hotfix package to your computer.
- Transfer the hotfix package to the Mobile Access Gateway (into some directory, e.g., /some_path_to_fix/).
Unpack and install the hotfix package:
[Expert@HostName]# cd /some_path_to_fix/
Note: The script will stop all of Check Point services (cpstop) - read the output on the screen.
[Expert@HostName]# tar -zxvf Check_Point_R77.30_Linux_sk107132.tgz
[Expert@HostName]# ./UnixInstallScriptReboot the Mobile Access Gateway.
UnInstall Instructions:
Note: In cluster environment, this procedure must be performed on all members of the cluster.
- Download and unpack the hotfix package (refer to the 'Installation instructions' above) above).
- Run the installation script with '-u' flag:
[Expert@HostName]# ./UnixInstallScript -u - Reboot the Mobile Access Gateway.
Related solutions:
Revision History:
Check Point Network & Wireless Cards Drivers
Show / Hide article revision history| Date | Description |
| 25 May 2017 |
|
| 01 Apr 2017 |
|
| 29 June 2016 |
|
| 10 Apr 2016 |
|
| 15 Mar 2016 |
|
| 25 Feb 2016 |
|
| 10 Feb 2016 |
|
| 13 Jan 2016 |
|
| 04 Jan 2016 |
|
| 17 Dec 2015 |
|
| 30 Nov 2015 |
|
| 23 Nov 2015 |
|
| 04 Oct 2015 |
|
| 27 Sep 2015 |
|
| 03 Sep 2015 |
|
| 10 Aug 2015 |
|
| 04 Aug 2015 |
|
| 03 Aug 2015 |
|
| 02 Aug 2015 |
|
- 01741975 , 01811969 , 01826267 , 01811958 , 01811956 , 01827887 , 01811964 , 01826091 , 01827270 , 01811963 , 01866679 , 01811957
- 01281853
- 00893066 , 01293972 , 01396838 , 01322548 , 01013933 , 01280147 , 01088030 , 01780359 , 01277999 , 01306045 , 01293973 , 01418332 , 01227825 , 01718569 , 01776720 , 01221649 , 01168834 , 01821996 , 01721715 , 01524000 , 01376279
